WISeKey’s secure elements to protect drones, their identification, remote control and data transmission

Industrial drone manufacturers realize that in order to have that cutting edge in their product portfolio, they need to look into the security of the drones they sell.
In the following you can read of typical scenarios for security shown at the industrial drone example but many other applications have very similar needs. Read here more about protection against counterfeiting by using dedicated WISeKey products.
Needs for Security
There are several topics that require security while operating a UAV, e.g.:
- Digital Remote Identification
- For the identification of the drone one expects integrity, authenticity, perhaps confidentiality and accountability. It is actually quite similar to a car license plate, that allows to find the regular operator and that no one wants to see spoofed;
- Remote Control
- Drone and remote control unit should be authenticated to one another so as to prevent a third party to take over the control of the drone in flight;
- Downlink data transmission
- Video or still images taken by the drone can be of a very sensitive or private nature. Therefore, this data shall be authenticated and protected against eavesdropping.
While security of other topics is of importance during maintenance or programming, e.g.:
- Firmware download
- If the firmware of the drone can be updated, it must not be possible by third parties to replace the drone-firmware with malicious code;
- Flight plan download
- Similar to the firmware update, any flight plan for autonomous flight shall be protected as to avoid third parties to alter it and have control over the drone.
All these concerns can be secured using state-of-the-art cryptography and communication protocols, implying the use of public key cryptography. The main caveat here is that drones are stored and used in mainly uncontrolled, hostile environments, in the sense that any malicious individual or group of individuals can easily obtain a drone, analyze it and find access to its sensitive assets, such as private keys needed for these security protocols.
WISeKey’s Secure Solution
Therefore, WISeKey offers its VaultIC408 as a secure companion chip to the drone’s main processor.
When delegating the cryptographic calculations and storage of the secret private keys to this Secure Element, the overall security of the drone can be guaranteed.
In fact the VaultIC408 is a tamper resistant secure element, certified by independent laboratories against the latest version of FIPS140-3.
Furthermore, VaultIC408 offers a wide variety of cryptographic algorithms and Elliptic Curves, as well as up to eight different user environments with each their own cryptographic parameters.
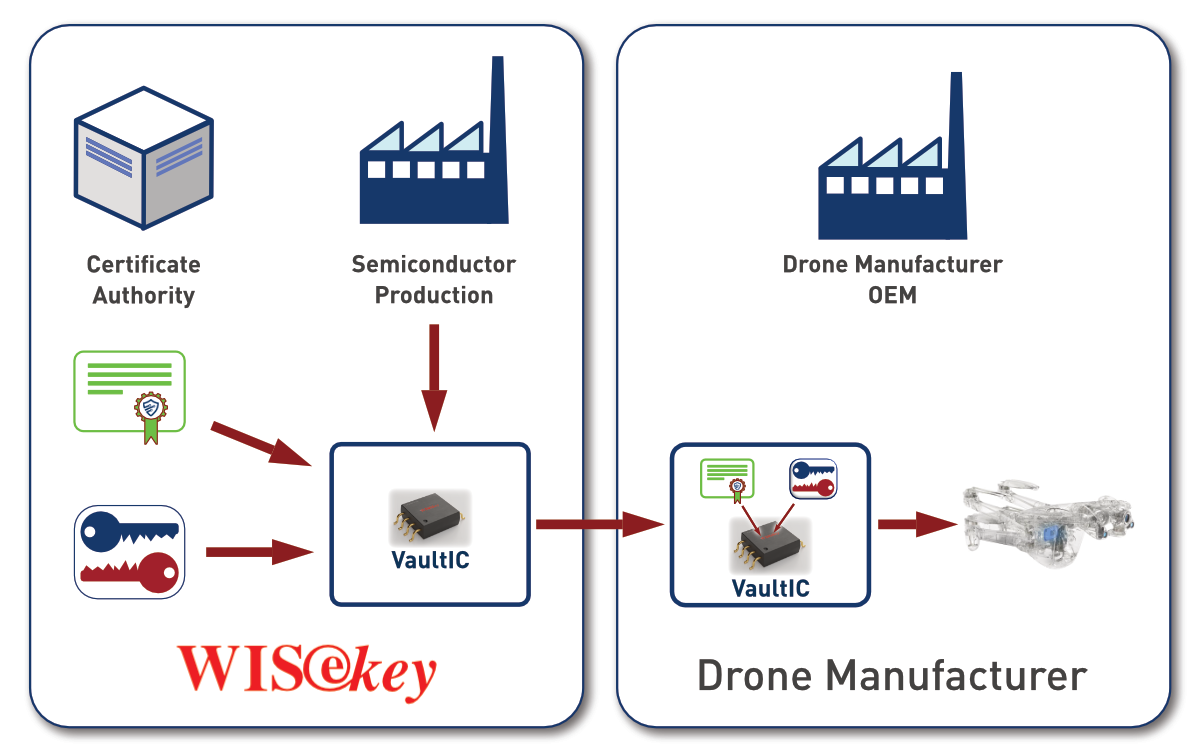
When it comes to manufacturing of the drone, the advantages of using a secure element are clear as well: Secret data, such as private keys and their related digital certificates are generated in WISeKey’s secure production facilities and stored inside the secure element during manufacturing. When it comes to building the drone, no security related secrets have to be processed by the OEM, as they will handle the secure element as any other chip on the PCB. The secrets are stored safely inside once they leave WISeKey.
Customers, such as the French Drone manufacturer Parrot rely on WISeKey for the security of their drones. Refer to this whitepaper for more information.
Key Features of VaultIC408
Cryptographic Services
- Strong generic challenge-response authentication protocol using digital signatures
- Digital Signature Generation / Verification
- Message Authentication Codes (MAC)
- Data encryption/decryption
- Key Agreement protocol
- Secure key transport with wrapping and unwrapping mechanisms
- Secure Communication Channel (MAC and encryption)
- One-Time Password Generation
- Message Digest
- On-chip public key pair generation
- NIST SP 800-90 Deterministic Random Bit Generator using AES-256 algorithm
- Strong authentication and secure communications for chip administration operations
- Secure data storage in dynamic file system
- Identity-based authentication and advanced access conditions
Software Features
- FIPS 140-3 Identity-based authentication using password, Strong Authentication with Secure Channel Protocol (SCP03)
- Rights Management (Administrator, Approved User, Non-approved User…)
- Embedded Dynamic File System
Cryptographic Algorithms
- AES 128/192/256 bits
- GCM / GMAC
- RSA® up to 2048 bits
- DSA up to 2048 bits
- ECC up to 576 bits over GF(p) and GF(2m)
Certifications / Standards
Memory
- Up to 16Kb dedicated to the File System
- EEPROM Data Retention : up to 50 Years
- Endurance : 500.000 write/erase cycles at 25°C
- Endurance : 200.000 write/erase cycles at 105°C
- 7-Slot ephemeral Key Ring
Package
- SOIC8 (RoHS compliant) 5mm x 5mm
- QFN20 (RoHS compliant) 4mm x 4mm
Hardware Platform
- 8-/16-bit RISC CPU
- Hardware Random Number Generator
- Hardware AES 128/192/256 Engine DPA/DEMA Resistant
- Hardware 32-bit Public Key Crypto Co-Processor
- CRC 16 & 32 Engine (Compliant with ISO / IEC 3309)
Security
- Dedicated Hardware for Protection Against SPA/DPA/SEMA/DEMA Attacks
- Advanced Protection Against Physical Attack, including Active Shield, Enhanced Protection Object, CStack
Checker, Slope Detector, Parity Errors (ROM, RAM)
- Environmental Protection Systems
- Voltage Monitor
- Frequency Monitor
- Temperature Monitor
- Light Protection
- Code Signature Module
Are you looking for a secure solution to protect your know-how or product brand, or should the topics presented in this article be considered in current developments? Talk to our team about the wide range of possibilities offered by the VaultIC family from WISeKey.


